The proliferation of hacking as a service is giving cybersecurity experts nightmares - The Economic Times
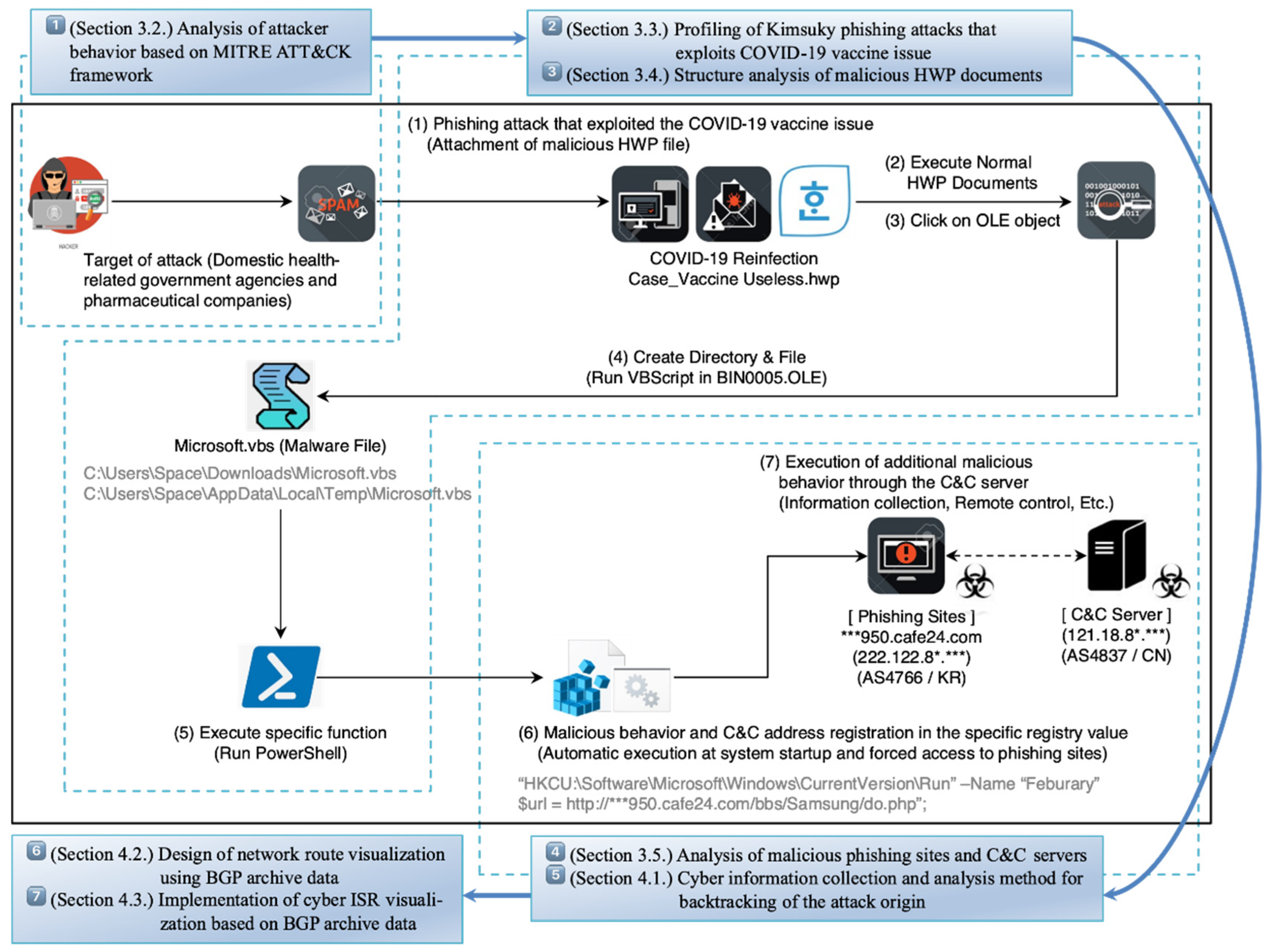
Electronics | Free Full-Text | Research on Cyber ISR Visualization Method Based on BGP Archive Data through Hacking Case Analysis of North Korean Cyber-Attack Groups

What can i do with the ssh host key i got from this nmap scan. (Hack the box) - Information Security Stack Exchange

Top 15 Security Utilities & Download Hacking Tools - Darknet - Hacking Tools, Hacker News & Cyber Security
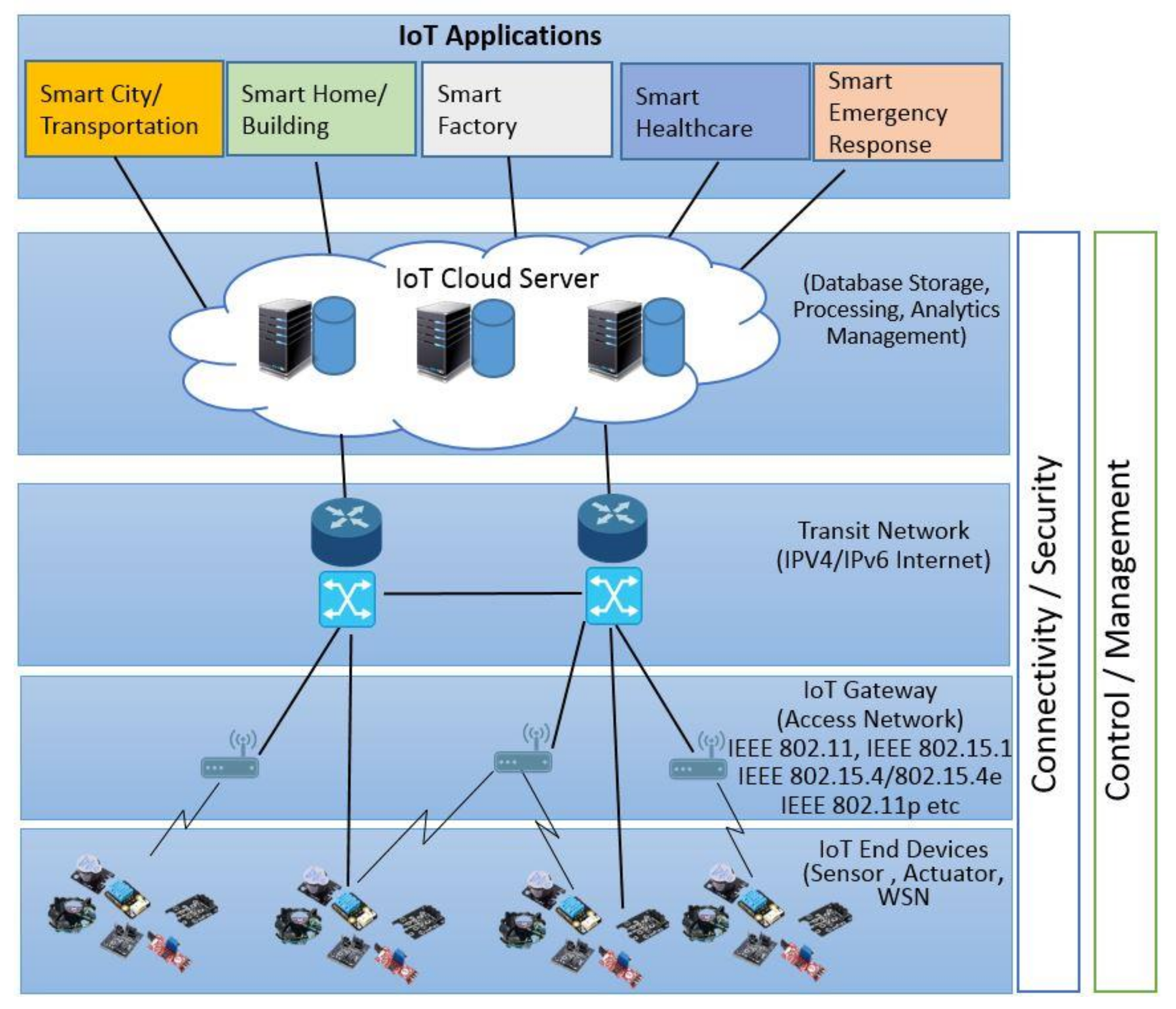
Electronics | Free Full-Text | An Overview of Medium Access Control and Radio Duty Cycling Protocols for Internet of Things